
[ad_1]
Remote is the new rule
The trend towards remote working has been steady for some time, and recent events are accelerating that pace. According to 2012 Gallup research, 39% of the U.S. workforce was working off-site at least part-time. By 2016, that number had risen to 43%1. It’s fair to assume that if the question was asked in 2020, that number will have grown dramatically.
While it’s impossible to predict what happens next, it’s clear that remote working will now be more permanent in many organizations. Whether it’s employees working from home, students engaging in distance learning, or family and friends catching up using web and video conferencing, there is in fact a new normal emerging: remote connectivity and collaboration.
New paradigm, new problems: securing the modern workplace
These cultural and organizational shifts have made confidential personal and business data a more attractive target for cybercriminals. Since traditional home networks are considered less secure than enterprise networks, remote users’ computer systems can be perceived as a weak security link and thus more prone to cyberattacks. According to a study, 86% of business executives agreed data breaches are more likely to occur when employees are working out of office2.
This move to more remote work also happens as cyberattacks are becoming increasingly sophisticated, with threats targeting low-level firmware becoming more prominent. To stay ahead of busy bad actors and ever-evolving threats, IT teams need to give end customers integrated hardware and software solutions that offer comprehensive security features for the entire system.
The AMD “Zen” advantage: comprehensive hardware-based security
While software security is important, it may be easily bypassed by exploiting known platform vulnerabilities. This is one reason hardware-based security (HBS) is gaining more importance. It works to complement software security and provides a stronger foundation for the whole platform by providing mechanisms to isolate critical data and workloads.
As a state-of-the-art hardware vendor in the PC, server, and console ecosystems, AMD plays a vital role in enhancing data security and protection by providing an architecture designed with security in mind. By combining hardware-based security features and associated software protections, AMD helps better protect users against many cyberattacks including sophisticated low-level firmware attacks.
The AMD “Zen” architecture has been designed with security features in mind, with a special focus on solutions to help protect user data and provide outstanding power and performance. It’s the “Zen” architecture that is the foundation the Ryzen™ and EPYC™ processors that have gained so much recent momentum in the PC/workstation/server space, as well as the foundation for some of the top next-generation gaming consoles.
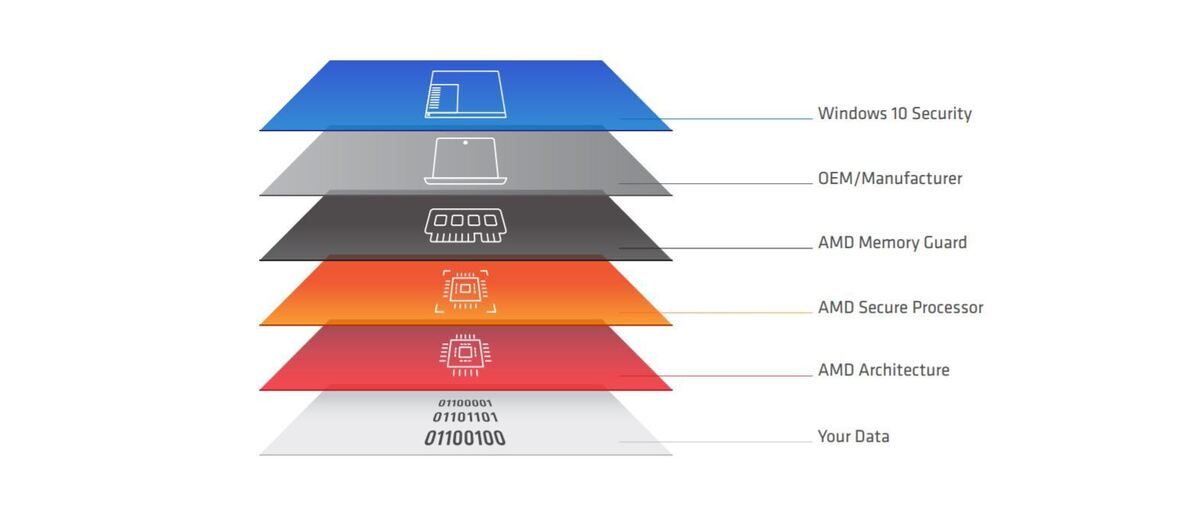
A layered, full-stack, defense-in-depth approach to security
AMD believes that the best modern security solutions can only be achieved through layered defenses. This is why AMD works closely with Operating Systems (OS) developers and PC manufacturers to provide architecture- and hardware-based security features that strengthen their own security offerings. By complementing these protections at various levels, AMD helps provide strong security against diverse and dynamic attacks.
Architecture Designed with Security in Mind
AMD “Zen” and “Zen 2”-based core architectures provide a strong security foundation. AMD’s security architecture helps to reduce exposure of attacks, can reduce downtime, may require fewer patches, and can help to improve the total cost of ownership.
Integrated Hardware Root of Trust
AMD keeps improving its silicon architecture with each generation, helping ensure the architecture is effective against future cyberattacks. Apart from strong architecture, each AMD silicon architecture ships out with a dedicated hardware security processor, the “AMD Secure Processor (ASP),” which acts as hardware root of trust. ASP provides platform integrity by authenticating initial firmware loaded on the platform.
The ability to authenticate each new system’s firmware means stronger protection from rogue or malicious firmware. If errors or modifications are detected, they are automatically denied access. This helps ensure a secure boot and protected operations.
Seamless Security Features, From Firmware to OS
Once the initial firmware and OEM BIOS are authenticated, control is passed on to OEM BIOS, which later passes on control to the OS. This way, a chain of trust is maintained across the platform, allowing malicious firmware to be easily detected and addressed. Each piece of physical security infrastructure complements the next layer, providing improved defenses.
A Critical Market First: AMD Memory Guard
AMD Ryzen™ Pro processors are the first commercial processors on the market to provide technology that helps protect user data by encrypting the complete system memory contents as a standard feature. AMD Memory Guard helps provide strong protection against cold boot attacks, DRAM interface snooping, and other similar exploits used to obtain user data. It’s also OS agnostic and transparent to software applications, helping increase data security from the ground up.
How it comes together: protecting busy users in a very mobile world
With so many people working remotely, from hotel rooms, airports, or coffee shops, data protection is critically important. Even normal operations can bring risk, if users unknowingly introduce compromised hardware or firmware to their device. That’s why an integrated chain of trust built around the AMD Secure Processor is so important. When used as the foundation for OS or manufacturer user identity and access protections, the complete, layered approach invisibly helps protect the computer from startup to shut down, all with outstanding PC performance.
But what about when things go wrong? Research shows that every 53 seconds a laptop is lost or stolen, putting confidential user at risk, making traditional security approaches inadequate3.
Why? Because when a laptop goes missing, software-based full-disk encryption (FDE) is typically the first line of defense in protecting user data. But it has limitations. Inside the computer, all of the data in system memory is in clear text, including cryptographic keys used for drive encryption/decryption. This means if a cybercriminal gains access to the computer, they can easily decipher those keys.
AMD Memory Guard helps prevent this from happening by encrypting the system information. This means when a laptop gets into the wrong hands, they can’t simply bypass full-disk encryption by accessing keys stored in memory. It’s a layer of encryption protection available with AMD Memory Guard4. And since its transparent to both OS and application, it can be easily enabled on any system.
Strengthening OS security
This multilayered, hardware-based security also provides significant benefits to the OS through underlying silicon features. Windows® 10 security features leverage this architecture to help provide a more fully protected computing experience to customers, no matter where they connect from.
Windows® 10 virtualization-based security (VBS) uses AMD-V with GMET to isolate a secure memory region from the normal operating system and prevents malicious applications and drivers from running or getting access to system memory. Similarly, the Microsoft Memory Access Protection feature provides security against DMA attacks, and is enabled by AMD-Vi with DMA remapping technology.
As a leading silicon provider to the PC markets, AMD’s innovation is key to enabling Microsoft Secured-Core PC, which helps protect your device from firmware vulnerabilities, helps shield the operating system from attacks, and can prevent unauthorized access to devices and data through advanced access controls and authentication systems. Secured-Core PC is enabled on AMD platforms via various technologies like AMD Dynamic Root of Trust Measurement (DRTM) and AMD SMM Supervisor.
“Microsoft and AMD partnered together to create a new class of enterprise devices called Secured-Core PCs based on the AMD Ryzen PRO platform. Together, we are developing products designed to protect commercial systems against sophisticated firmware attacks and provide simple and secure PC experiences to enterprise customers,” said David Weston, Director of enterprise and OS security, Microsoft.
As threats evolve, so do AMD security features
AMD approaches security with a relationship mindset. By providing a strong, hardware-based security architecture foundation, AMD enables PC manufacturers and OS developers to leverage these features when building their own features and functions. The end result is security features to help keep information secure no matter where the user works.
This seamless approach to security is more important than ever. Organizations are facing a threat landscape that is continuously evolving in both size and complexity, and users who are demanding new ways of connecting and collaborating. To help keep them safe, a single level or layer of protection is not sufficient. The AMD layered security features strategy, along with AMD’s modern core architectures and AMD Memory Guard, help provide security features to end customers and help protect their data.
1https://www.gallup.com/workplace/283985/working-remotely-effective-gallup-research-says-yes.aspx
2https://www.shredit.com/en-us/resource-center/original-research/security-tracker-2018
3https://www.channelpronetwork.com/article/mobile-device-security-startling-statistics-data-loss-and-data-breaches
4Full system memory encryption with AMD Memory Guard is included as a standard feature with AMD Ryzen PRO, AMD Ryzen Threadripper Pro, and AMD Athlon PRO processors. PP-3.
[ad_2]
Source link