
[ad_1]
There are errors (bugs) and safety vulnerabilities within the code of virtually all software program. The extra intensive the code, the extra there are. Many of those safety flaws are found over time by customers and even by the producer itself and plugged with a patch or the subsequent replace. Some, nevertheless, are first tracked down by prison hackers who first preserve this data to themselves. They then both use the safety gap themselves to penetrate different individuals’s methods, or they promote their discover, typically for horrendous sums.
What is a zero day flaw?
Such newly found safety vulnerabilities are referred to as zero days, typically additionally spelled 0-day. This refers back to the period of time the producer has to shut the hole. “Zero days” implies that the corporate has no time in any respect to develop a patch and publish it. This is as a result of the hackers are already actively exploiting the vulnerability. To accomplish that, they use a zero-day exploit, i.e. a way specifically developed for this vulnerability, and use it to hold out a zero-day assault.
As quickly because the software program producer learns concerning the vulnerability, it could possibly develop a patch that particularly modifications the accountable a part of the code. Or it publishes an replace, i.e. a revised and cleaned-up model of his program. As quickly as a patch or an replace exists, the exploit is not efficient, the zero-day risk is formally over.
However, since many customers don’t apply patches instantly, however solely after a number of days or perhaps weeks delay, the hazard posed by the vulnerability stays for some time.
Zero-day assaults are among the many most harmful of all. Because so long as the vulnerability is unknown to producers and customers, they don’t take any preventive protecting measures. For days, typically weeks or months, the attackers can scout out different individuals’s laptop methods unnoticed, acquire larger rights, obtain confidential information, or set up malware. Anti-virus instruments are designed to detect such actions. Nevertheless, attackers succeed again and again in disguising themselves so properly that they often stay undetected.
Further studying: The best antivirus software for Windows PCs
Coveted secret data: Prizes of one million and extra
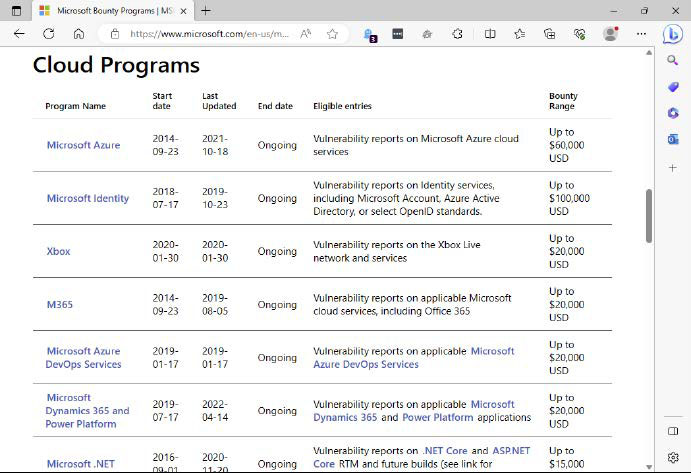
On its bug bounty web site, Microsoft lists the utmost sums it’ll pay for newly found safety holes. For some merchandise, the finder can rise up to 100,000 US {dollars}.
IDG
A zero-day safety vulnerability has a excessive worth on the black market. Six- to seven-figure sums are supplied on the darkish net for a newly detected and never but patched safety gap in Windows. But it’s not solely criminals who’re within the vulnerabilities. In the previous, secret providers additionally exploited the gaps to hold out assaults on databases and infrastructure of different states.
The best-known instance is Stuxnet: A pc worm reportedly developed by Israel and the USA was infiltrated into the methods of the Iranian nuclear program. Through a number of beforehand unknown safety holes in Windows, it managed to take root within the system. It then manipulated the management of centrifuges for the manufacturing of fissile materials in order that they have been faulty after a short while, however didn’t difficulty an error message.
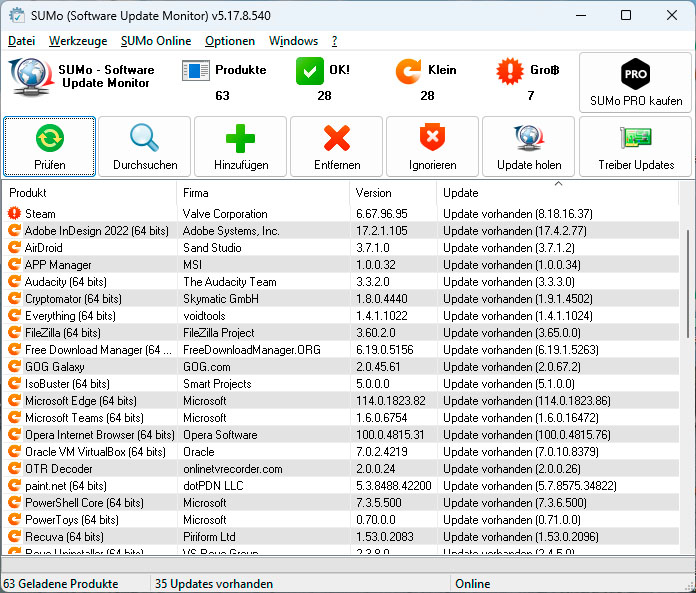
With the free instrument Sumo, you will discover out for which of your programmes updates can be found after which set up them particularly.
IDG
Governments and firms additionally use zero-day vulnerabilities for industrial espionage, i.e. to faucet into plans for brand spanking new developments, firm information, and speak to addresses. And lastly, hacktivists additionally resort to this implies to attract consideration to their political or social objectives.
Due to the excessive hazard potential of zero-day flaws and the excessive sums paid for his or her disclosure, a number of giant software program corporations have launched bug bounty packages. This “bounty for bugs” is paid by producers like Microsoft for newly found safety holes and different bugs of their working methods and purposes. The bounties are largely based mostly on the severity of the bug and vary from three to 6 figures.
Attention: The 5 most dangerous Wi-Fi attacks, and how to fight them
How to detect zero-day assaults
When trying to find malware, trendy antivirus packages work not solely with virus signatures, but in addition with heuristic strategies and synthetic intelligence. The producers practice them with the behavioral patterns of recognized malware so as to have the ability to detect new variants. However, this solely works to a restricted extent, as zero-day exploits all the time use totally different assault strategies.
Behavior-based safety options are sometimes utilized in corporations. Intrusion detection methods monitor log information and system data similar to CPU utilization to establish conspicuous actions inside a community and on particular person computer systems. In this case, they difficulty a warning message or ship an e-mail to the administrator. Intrusion prevention methods go one step additional and routinely set off countermeasures similar to modifications to the firewall configuration. However, such purposes are very costly and solely appropriate for companies.
Finding details about new safety vulnerabilities
Until the late Nineties, safety vulnerabilities weren’t systematically recorded. But as new vulnerabilities have been discovered within the quickly rising variety of Windows purposes, two staff of the Mitre Corporation started to consider a smart system for recording and managing them.
The US Mitre Corporation was based in 1958 as a suppose tank for the US armed forces and as we speak advises a number of American authorities on safety points. The non-profit group is funded by CISA (Cybersecurity and Infrastructure Security Agency) and DHS (Department of Homeland Security).
The results of the deliberations was the CVE system (Common Vulnerabilities and Exposures) launched in 1999. Since then, all safety vulnerabilities have been given a CVE quantity or ID within the format CVE-XXXX-XXXXX. The first 4 characters point out the 12 months through which the vulnerability was catalogued, the digits behind it – there could also be greater than 5 – are the consecutive numbering of the vulnerability. The CVE system has in the meantime developed into an internationally recognised customary.
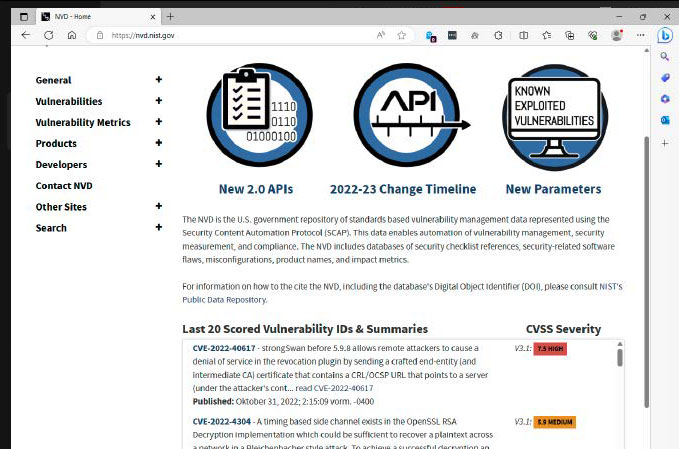
The National Vulnerability Database of the USA reveals the 20 most just lately discovered vulnerabilities and their CVE numbers. In addition, there’s data on the mode of motion and any accessible patches.
IDG
The Mitre Corporation has arrange the web site www.cve.org for the CVE database. There you’ll be able to seek for CVE numbers or for key phrases similar to “Windows Kernel”.
Alternatively, you’ll be able to obtain your complete database with its greater than 207,000 entries. Closely linked to the CVE web site is the National Vulnerability Database (NVD). At https://nvd.nist.gov one can find the 20 most just lately recognized vulnerabilities, together with some explanations and hyperlinks to any accessible patches.
There additionally, you will discover an evaluation of the hazard of the vulnerability from “Low” to “Medium” to “High” and “Critical”. If an software you employ seems there whose vulnerability is marked as “High” or “Critical”, examine the producer’s web site to see if a patch is already accessible.
Microsoft additionally makes use of the CVE customary, however maintains its personal record of newly detected vulnerabilities for its merchandise at https://msrc.microsoft.com/update-guide/vulnerability The firm distributes patches routinely by way of its month-to-month safety updates; guide set up just isn’t crucial.
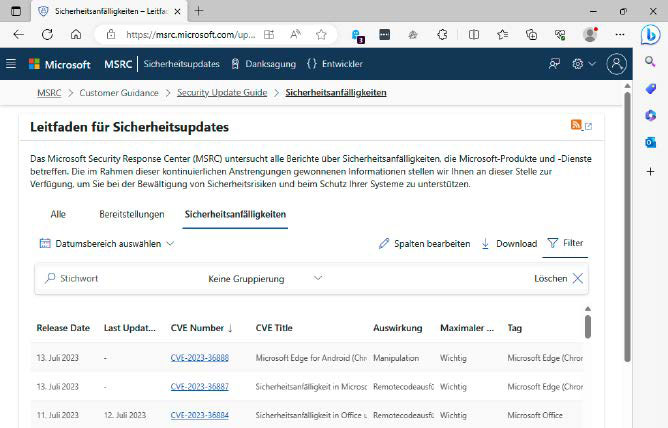
The firm publishes newly discovered safety vulnerabilities in its merchandise within the Microsoft Security Response Center. You don’t want to fret about putting in the patches, that is completed routinely.
IDG
How to guard your self from zero-day exploits
Zero-day assaults aren’t solely directed towards corporations. Hacker teams typically additionally attempt to lure non-public customers to malicious web sites by way of extensively distributed phishing assaults by e-mail, or to steer them to put in software program with zero-day exploits, typically by way of scammy Google ads.
You can shield your self with a number of easy measures:
- Install patches and updates as quickly as they seem. Windows does this routinely by default, so you shouldn’t change something. Use instruments like Sumo to seek for accessible updates for Windows purposes.
- Only obtain software program from reliable sources such because the producer’s web site.
- Only set up the packages you really want. The extra software program there’s on the pc, the extra potential vulnerabilities there are.
- Use a firewall. The Windows firewall is switched on by default and shouldn’t be deactivated.
- Find out about typical phishing tricks utilized by criminals.
What to do if there are issues with updates?
You ought to all the time set up the month-to-month safety updates and patches for Windows instantly in an effort to eradicate newly detected vulnerabilities.
However, the set up of a Windows replace just isn’t all the time profitable. Sometimes the working system aborts the method with an error message. In such a case, strive the next:
1. Often, merely downloading the replace information didn’t work. The resolution is to empty the replace cache and check out once more. The simplest way to do that is by way of the Windows troubleshooter: Call up the “Settings” within the Start menu and click on on “Troubleshooting -‘ Other troubleshooting” within the “System” tab. Then click on on “Run” for “Windows Update” and at last on “Close”. Then restart Windows by opening the “Run” window with the Windows-R key mixture, typing the command shutdown /g and clicking “OK”. Then attempt to set up the updates once more.
2. Often there’s merely no more room on the C: drive. Check this by opening the Explorer and choosing “This PC”. There ought to nonetheless be at the least 32GB free on C:. If not, open the “Memory” choices within the “Properties” beneath “System” and set the “Memory optimisation” change to “On”. Click on “Clean-up recommendations” and look specifically on the gadgets “Large or unused files” and “Unused apps”. You also needs to empty the Windows Recycle Bin.
Michael Crider/IDG
3. Try a guide set up of the replace. Look within the “Settings” beneath “System -‘ Windows Update” in addition to beneath “Update history” for a message a couple of failed replace. Make a be aware of the KB variety of the replace and enter it within the Windows replace catalogue at www.catalog.update.microsoft.com. Make certain that the replace matches your Windows model, obtain it and set up it manually.
4. If you employ a virus scanner apart from Microsoft’s Defender, you need to uninstall it quickly. Then restart Windows and attempt to run the replace.
5. Disconnect any related USB gadgets similar to flash drives or exterior storage.
6. Open the Windows Control Panel (the simplest method to do that is by coming into “control” within the search discipline of the taskbar) and name up the Device Manager. If entries with a query mark seem there, take away this {hardware} by right-clicking and choosing “Uninstall device”. Then attempt to run the replace. When you restart, Windows will then acknowledge the gadgets once more and set up the newest drivers.
7. Update the drivers in your laptop. Use a instrument similar to Driver Booster Free to examine for outdated driver variations. Download the newest variations, set them up and check out putting in the Windows replace once more.
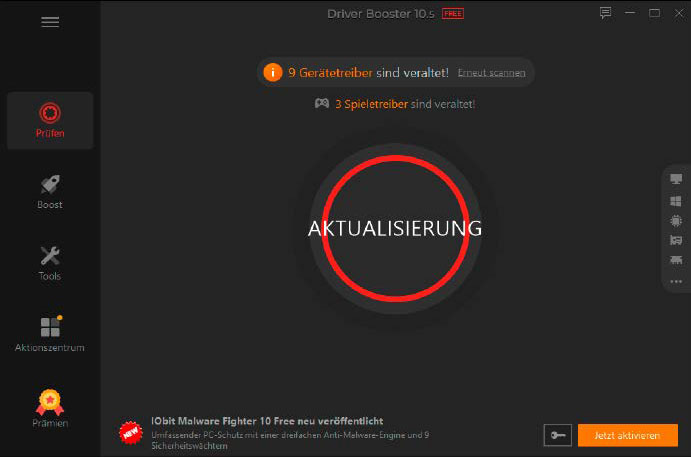
Make certain your drivers are updated. For instance, the instrument Driver Booster Free can assist you seek for outdated variations.
IDG
This article was translated from German to English and initially appeared on pcwelt.de.
[adinserter block=”4″]
[ad_2]
Source link