
[ad_1]
I’ve been working within the IT business for over 30 years, for many of this time as an editor at PC-WELT (PCWorld’s German sister publication), specializing in safety. I check antivirus software program, give recommendations on the best way to make Windows safer, am continuously looking out for the perfect safety instruments, and monitor the actions of cyber criminals.
Over the years, I’ve acquired an entire vary of behaviors and rules that appear utterly regular and smart to me. However, once I observe different PC customers, I typically uncover dangerous or a minimum of much less security-oriented conduct.
That’s why I’ve put collectively the ten most essential issues I might by no means do as an IT safety professional.
Further studying: Best antivirus software
1. Move as a substitute of copy
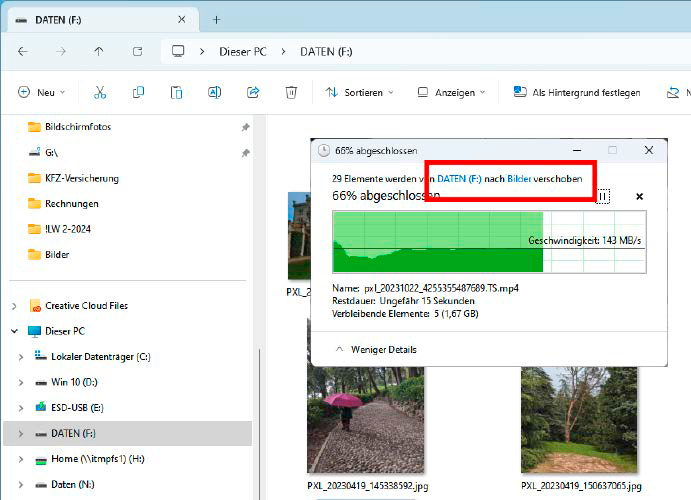
You can hardly inform the distinction in Windows Explorer: Here, images and movies are moved as a substitute of copied. This can worsen information safety relatively than enhance it.
IDG
Moving your personal recordsdata as a substitute of copying them instantly makes me really feel uneasy. This contains, for instance, images or movies from the digicam or audio recordings from a smartphone or audio recorder. If you progress such recordsdata, that are normally distinctive, you run the chance of shedding them as quickly as you progress them. Although that is very uncommon, it can’t be utterly dominated out.
But even when the shifting course of goes easily: The information is then nonetheless solely out there as soon as. If the onerous drive within the PC breaks, the information is gone. If I make a mistake and unintentionally delete the recordsdata, they’re gone. These are dangers that solely come up for those who begin a transfer operation as a substitute of a replica operation.
If you assume: I would like the house on the SD card for brand spanking new images, you must contemplate shopping for a second SD card. Your personal information is all the time value it.
And when do I launch the house on the SD card? I do that as quickly as my backup plan on the PC has backed up the copied information. In my case, that is performed on a tough drive within the community that runs on a Raspberry Pi.
Important recordsdata are additionally mechanically encrypted and uploaded to cloud storage.
Further studying: Best online backup services
2. Save my very own information and not using a backup
I’ve arrange an automatic backup for all important data. Because saving recordsdata I’ve created myself and not using a immediate backup is much too dangerous for me. This additionally contains all information that I enter into apps, for instance, whether or not for Android, iOS, or Windows. Just as a result of most apps don’t supply an simply recognizable backup operate doesn’t absolve the person of duty for his or her information.
For instance, at two grammar faculties in Koblenz, Germany, a number of hundred faculty iPads have been logged off the college community as a consequence of an error. The handwritten notes within the Goodnotes app utilized by the pupils have been deleted. Many college students had labored solely with the college’s personal iPads and this app — in different phrases, there was no secondary copy of their notes. Around 500 of the entire of seven,500 iPads have been affected by the information loss by being linked to the college community on the time of the breakdown.
A cloud backup, as is common for iPads, was deactivated for information safety causes. No different type of information backup seems to have been used. The pupils involved can’t be blamed right here, however the system administrator accountable can.
3. Format and not using a thorough examine
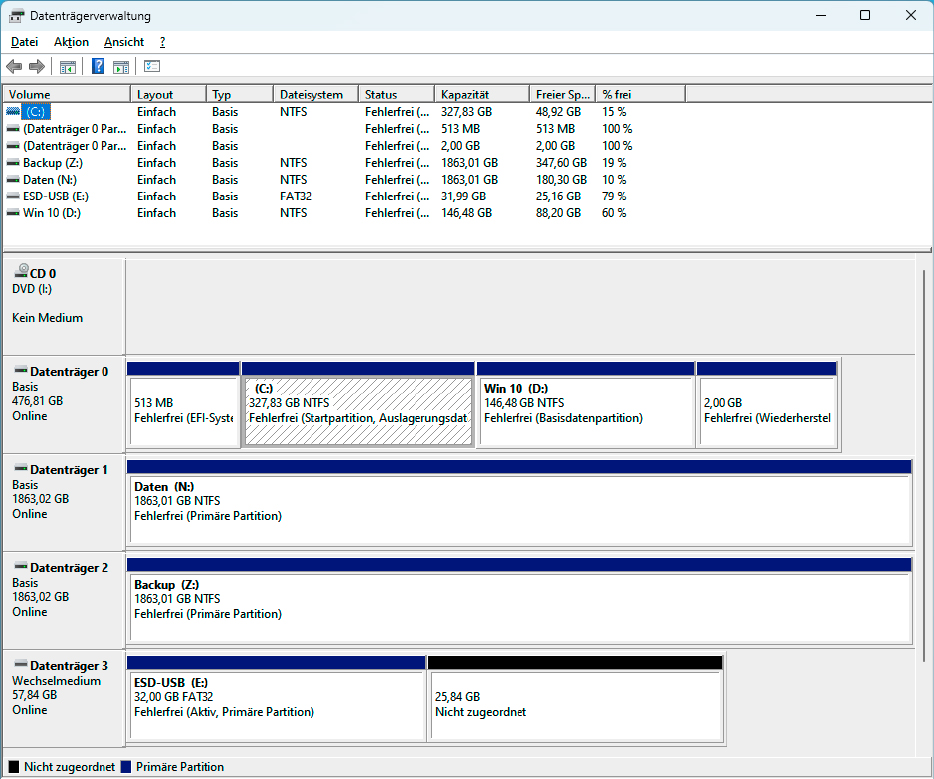
The drive administration reveals every linked drive with all partitions. You can normally clearly determine a partition primarily based on its title and measurement.
IDG
I might by no means make this error — as a result of I’ve made it earlier than. Therefore, I can solely advise from expertise: Only format a storage drive when you find yourself positive that you’ve got chosen the proper drive.
For years, I used exterior USB onerous drives to retailer my recordsdata. The folder construction on these onerous drives was normally equivalent. There have been the folders “My Documents,” “Videos,” “Temp,” “Virtual PCs,” and some extra. What’s extra, all of the onerous drives have been the identical mannequin, which I had as soon as purchased generously on a great deal. Some of those disks even had the identical information provider designation — particularly “Data.”
That wasn’t very intelligent, as a result of it made it too simple to combine them up. So I ended up complicated certainly one of these onerous drives with one other one at a late hour and formatted the mistaken one.
Since then, I’ve named and labelled my exterior onerous drives and USB sticks very clearly and take one other shut look earlier than formatting them.
First examine, then format: Choosing the proper drive earlier than formatting is essential to keep away from unintentional information loss. In Windows Explorer, examine which drive letter the onerous drive or partition to be formatted has. This is commonly not instantly obvious on methods with a number of drives. Take the time to examine, unplug different onerous disks and drives to extend the overview. The title of the disk and its measurement will allow you to to determine it.
In addition, begin Disk Management by coming into Disk Management within the Windows search. All linked disks and their partitions can be displayed. Only begin formatting when you find yourself positive that you’ve got discovered the proper onerous drive, USB stick, or partition.
4. Open hyperlinks in emails
I don’t prefer to open a hyperlink in an e mail. And I by no means open a hyperlink if the e-mail is supposedly from my financial institution or cost service supplier. I don’t even open the hyperlink within the month-to-month e mail from PayPal, despite the fact that I do know that this e mail truly comes from PayPal.
Why not? Nowadays it is extremely simple for an attacker to create a deceptively actual copy of a financial institution e mail. I wouldn’t reliably acknowledge the distinction between a phishing e mail and an actual financial institution e mail — a minimum of not within the quick time I’ve to examine my inbox.
Instead, I open on-line banking pages and different essential pages through hyperlinks I’ve saved in my browser, or retype the deal with into the browser every time. I log in to the positioning and examine whether or not a brand new message has arrived in my buyer account. If not, then the message within the e mail is both a pretend or not essential sufficient for the financial institution to enter this data in my buyer account. That’s the tip of the matter for me.
Tip: Change these 5 Windows settings to improve your data privacy
5. Opening suspicious recordsdata
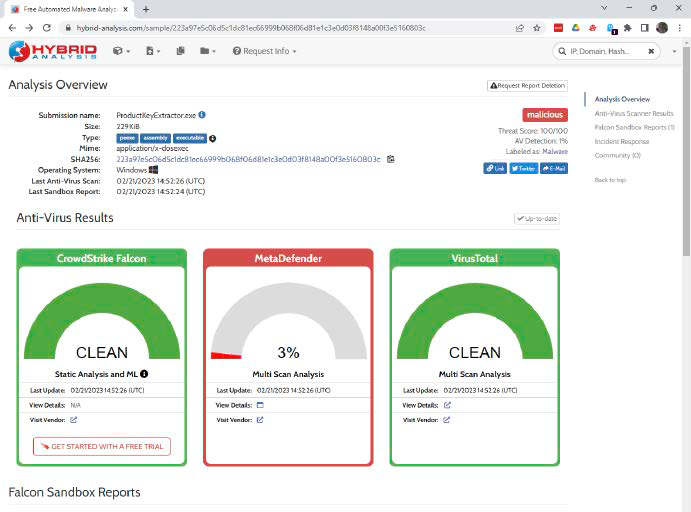
The on-line sandbox Hybrid Analysis paperwork the conduct of a suspicious program with a screenshot. The service is free, however it’s typically overloaded and responds very slowly.
IDG
If a file is suspicious, no matter whether or not it’s a program or a doc, I don’t open it. The danger is just too nice. As an IT editor, I’m after all continuously downloading instruments from the web and fairly a couple of of them are scanned by the virus scanner. That is one indication that makes a file suspicious.
Another is the supply. Files from doubtful web sites are simply as suspicious as recordsdata which might be hooked up to an e mail or come from hyperlinks in emails. If I can’t keep away from opening or beginning such recordsdata, I all the time examine them first with the instrument www.virustotal.com. The on-line service checks a file with greater than 60 virus scanners.
If you need much more details about a suspicious file than www.virustotal.com gives, it’s also possible to add suspicious recordsdata to a web based sandbox. However, that is considerably extra sophisticated than a check at Virustotal. The companies typically require registration and are generally topic to a price.
A free and uncomplicated on-line sandbox with out registration is obtainable at www.hybrid-analysis.com.
6. Give vouchers for cost of companies
If you’re requested to purchase vouchers, you must hear rigorously (a minimum of if the request doesn’t come out of your youngsters). This is how scammers who’re after your cash function.
Foundry
Who would need to do that? An astonishing variety of customers! They are all victims of a social engineering assault. Social engineering makes use of psychological tips to control folks into doing issues that aren’t of their pursuits. Human traits corresponding to belief, worry, or ignorance are exploited.
A well-liked trick goes like this: You are browsing the web and abruptly a warning message seems that seems to return from Windows. Your PC has been hacked and you must name a help phone quantity so {that a} Microsoft worker can repair your PC. When you name, you’re informed that your PC has truly been hacked. However, this prices cash and is meant to be paid for with voucher playing cards. The criminals demand these as a result of voucher codes are a lot tougher for the police to hint than a financial institution switch.
The truth is: Nobody is resistant to the tips of social engineering. A well-prepared and skillful attacker can lure anybody right into a lure. There are many examples of this — search “CEO fraud.” But the second one thing as uncommon as a voucher code for a service is requested, you may change into suspicious and escape the lure. The similar applies in case you are informed that somebody is coming spherical to gather cash from you.
See additionally: How do I remove malware from my PC?
7. Connect unknown exterior gadgets
A USB stick whose proprietor I don’t know. I’m not plugging it in. Fortunately, gone are the times when Windows’ autostart operate instantly launched an EXE file from a linked USB stick. By default, Windows 10 and 11 solely supply to begin Windows Explorer to show the contents of the USB stick.
So that’s not the issue. But like everybody, I’m curious. Attackers reap the benefits of this and save malicious recordsdata with file names you can’t resist opening.
For a very long time, safety specialists stated that for those who wished to interrupt into an organization community, all you needed to do was go away a couple of contaminated USB sticks within the firm parking zone. Some worker will seize a stick and join it to their work PC.
The skilled malware Stuxnet can be stated to have reached the computer systems on the Iranian nuclear facility through a USB stick. It is barely unclear whether or not this USB stick bought into the plant through the parking zone trick or whether or not an insider smuggled it in. Stuxnet destroyed the centrifuges within the nuclear facility and thus delayed the manufacturing of fissile materials for a nuclear bomb.
When it’s important to insert a international USB stick: The similar guidelines apply as beneath level 5. Check the recordsdata on www.virustotal.com or begin them in a sandbox.
8. Use default passwords
When I join a brand new machine that has default password safety, I instantly change the present password. The similar applies to on-line accounts which have given me a password.
Admittedly: It has change into uncommon for a router to return with a default password. However, it’s all the extra essential to behave rapidly within the remaining circumstances. This is as a result of attackers know the default passwords and attempt to use them to log into the gadgets. A great password manager may help you create robust, distinctive passwords for each web site and repair you employ.
9. Enable pointless community companies

If you do not want distant entry to the Fritzbox through www.myfritz.web, for instance, you shouldn’t activate it. Every entry level to your IT will increase the assault floor for hackers.
IDG
Hardly a month goes by and not using a new safety vulnerability in a NAS or webcam turning into recognized. These community gadgets are normally weak through the web and permit hackers to entry the information on the NAS, the pictures on the webcam, and even your entire house community.
That’s why I don’t activate any community companies that I don’t want. Remote entry to my router — deactivated. Remote entry to my sensible lighting — deactivated. Access to my NAS and the robotic vacuum cleaner can be deactivated.
10. Buy an costly Plus model of antivirus
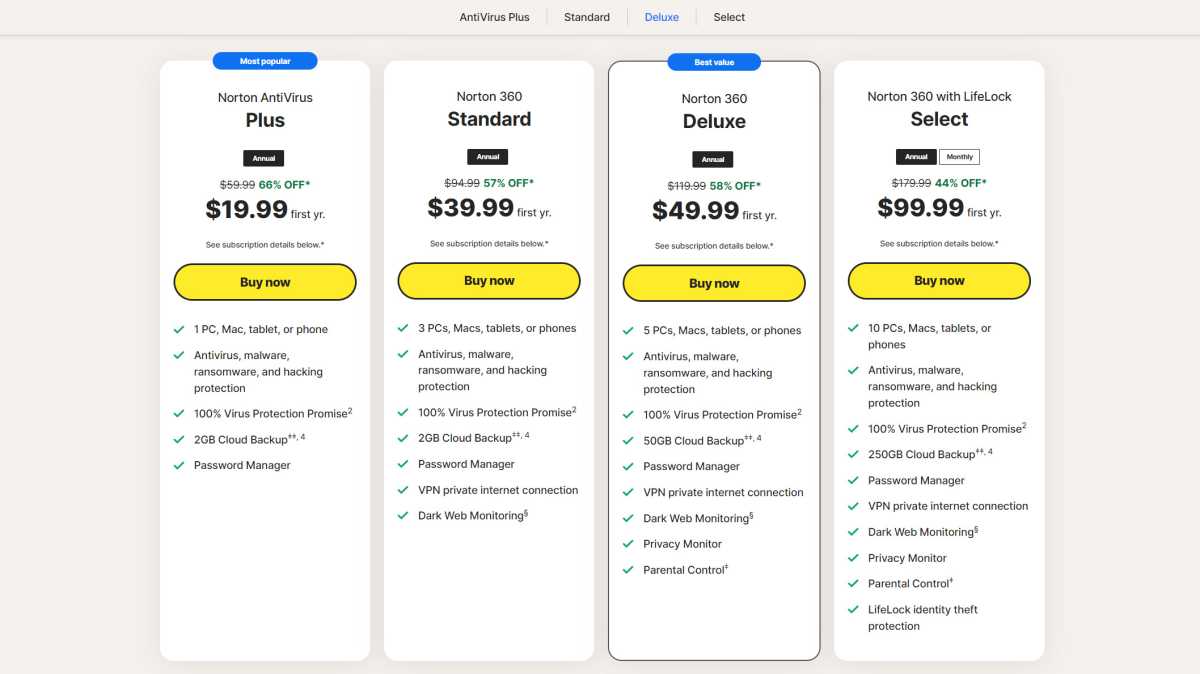
Most antivirus producers supply three or extra program variations. I wouldn’t purchase the most costly one. I don’t want their costly extra features.
PCWorld
Antivirus software program is normally out there in three variations. Simple, good, and excellent — or antivirus, web safety, and complete safety. I might by no means purchase the third and costliest model.
That’s purely a monetary consideration: If I have been wealthy, I might resolve in another way. But so long as cash is tight, I solely purchase the center variant, which is normally referred to as Internet Security. It normally affords greater than the free Microsoft Defender, however is just not as costly as the complete model.
With the latter, I might be paying for companies that I don’t essentially want (metadata cleaning, social media monitoring) or that I can get cheaper elsewhere (VPN services, cloud storage).
As I stated, the entire variations supply extra, however I don’t want that additional.
This article was translated from German to English and initially appeared on pcwelt.de.
[adinserter block=”4″]
[ad_2]
Source link