
[ad_1]
Still a devoted WinRar consumer? You must replace your software program proper now, particularly for those who’ve received cryptocurrency. A zero-day vulnerability in WinRar has been permitting hackers to interrupt into buying and selling accounts, and so they’ve been actively working this exploit since April. New data in October 2023 signifies that state-level hackers are actively exploiting this bug. The similar vulnerability may very well be used to put in different sorts of malware in your system as effectively.
The approach it really works: You open a malicious zip file in WinRAR, which is your default program for all compressed file codecs in your PC (after you’ve put in WinRar, after all). It’s stuffed with seemingly harmless paperwork—PDFs, textual content information, JPG photos. You double-click on one to open it, which it does. But unbeknownst to you, WinRAR was additionally tricked into loading a script within the background, which installs malware that lets attackers steal cash from brokerage accounts.
As reported by Bleeping Computer, WinRAR model 6.23 fixes this challenge together with others, like a flaw that permits instructions to be executed for those who open sure sorts of rar information. (That is, RAR information created in a selected solution to exploit that flaw.) It launched on August 2 and must be out there to all WinRAR customers. The newest release, 6.24, additionally addressed the safety challenge. You’ll must manually obtain the newer variations, and WinRAR lacks an automated replace operate.
Group-IB (by way of Bleeping Computer)
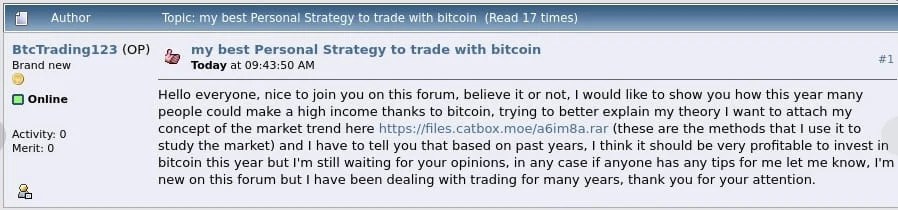
Cybersecurity firm Group-IB discovered this vulnerability (filed as CVE-2023-38831) whereas monitoring the unfold of the DarkMe malware household, which has been linked beforehand to monetary assaults. The tainted zip information, which have been posted on boards for cryptocurrency and inventory buying and selling, contained DarkMe and different malware households like GuLoader and Remcos. The latter two households permit extra malware to be downloaded and put in in your PC, in addition to giving the flexibility to run any command, file keystrokes, display screen seize, handle information, and extra to the attacker. (For deeper technical particulars, try Bleeping Computer’s rundown of the exploit.)
At the time of Group-IB’s report, 130 merchants have been confirmed as contaminated. The zip information have been shared on not less than eight boards, all underneath the guise of serving to others enhance their earnings. Currently, the complete sufferer depend and quantity of monetary damages are usually not but recognized. Since WinRAR doesn’t embody an automated replace operate, all customers are suggested to manually obtain and set up the newest model.
If nothing else, this WinRAR assault is one more reminder that the outdated safety tip of by no means downloading unusual information off the web (a lot much less opening) them nonetheless stays true. It may also be seen as extra incentive to improve to Windows 11, which is able to quickly natively support compressed file codecs like rar, 7-Zip, and gz—no want for third-party software program.
This article was initially printed on August twenty third, 2023, and up to date with new data on October nineteenth, 2023.
[adinserter block=”4″]
[ad_2]
Source link