
[ad_1]
Time and time once more, there are stories of a brand new firm that has suffered a pc breach the place hackers have obtained person account info. Databases containing thousands and thousands of login particulars are brazenly circulating on the web and present the extent of the issue. It doesn’t matter how lengthy your password is that if the corporate doesn’t shield it.
Moreover, most individuals as we speak haven’t only a few however tens or a whole lot of accounts on totally different web sites. Some will not be that essential, however many are. Either by their nature, like electronic mail and social media, or due to what they include and their sentimental worth to you. Imagine you’ve spent 20,000 hours on an internet role-playing sport and out of the blue hackers get in, change your password and electronic mail handle and rename your character “Same password everywhere.” Bummer.
Hackers aren’t simply searching for monetary accounts, emails, and social media. They additionally hunt accounts in varied digital shops, with Steam accounts with many video games being significantly wanted, and a few wish to lock victims out of boards and different accounts that don’t have any worth to anybody however the sufferer.
In this information, I stroll you thru what you may and may do to guard your self as a lot as potential from shedding any accounts to hackers.
Further studying: 4 dangerous PC security exploits attacking right now (and how to fight them)
Foundry
Use distinctive, robust passwords
Firstly, what ought to have been drilled into each web person’s head by now: You really want to keep away from having the identical password on a couple of account. For accounts you actually don’t care about, it might not matter a lot, however all of the accounts you’d hate to lose management of you need to merely have a singular password. Bottom line.
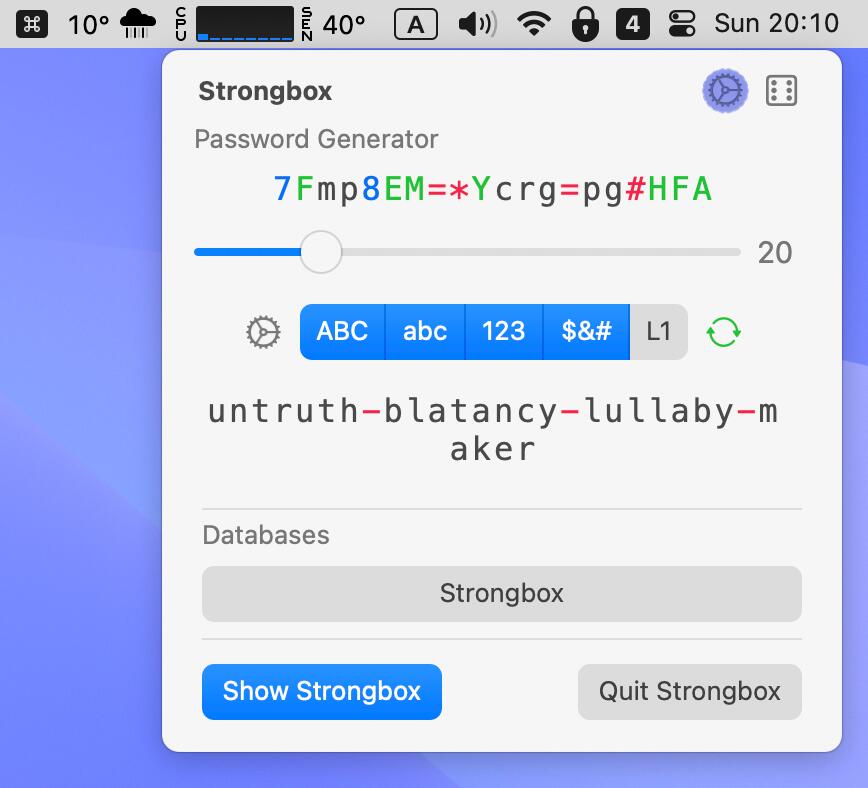
As effectively as being distinctive, it’s essential that the password is robust sufficient that it may’t be simply guessed. There are totally different faculties of thought on this. Some assume that a couple of random phrases are simpler to memorize if wanted, and simpler to kind in. Others favor a random string of characters and numbers. If you ever must enter your password manually and never through a password supervisor (see beneath), I like to recommend the phrase mannequin.
Strong passwords aren’t nearly maintaining individuals out of your account. Almost as essential is that hackers who come throughout an organization’s person database usually need to crack (guess) every account’s password, as these should not saved in plain textual content however as so-called hash codes.
Foundry
A password supervisor is a giant assist
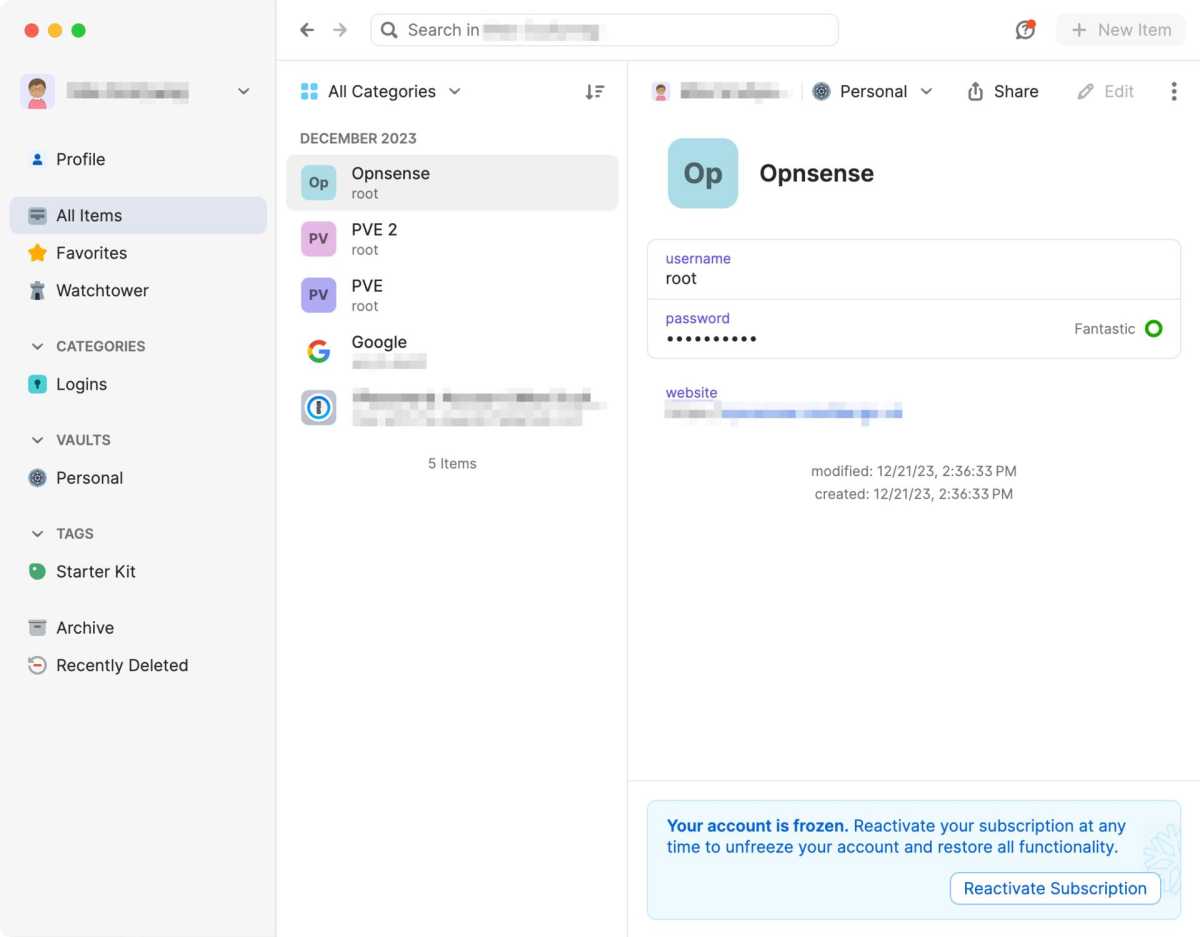
To preserve monitor of so many accounts, every with a singular password, most individuals need assistance, and one of the best assistance is a password supervisor. There are many to select from, however what they’ve in widespread is that they’re extra handy and safer than letting your browser save your passwords.
Further studying: The best password managers
All good password managers have a couple of issues in widespread. They retailer all information encrypted and deal with all of the encryption and decryption in your gadgets in order that the developer — or a hacker who has damaged into the developer — can by no means see any passwords. They can generate new robust passwords and robotically save them. They robotically fill within the information, however solely on the proper web site. And lastly, they will synchronize passwords between totally different gadgets, so you may simply log in to your accounts irrespective of which gadget you employ.
Another useful characteristic of some password managers is the power to retailer issues apart from passwords — passports, checking account and debit card particulars, safe notes, and anything you need to preserve organized and don’t need outsiders to eavesdrop on.
Foundry
Two-factor authentication and two-step verification
Strong passwords shield in opposition to some threats, however not all. For instance, malware that screens the whole lot you kind in your keyboard can learn passwords. Phishing web sites can trick you into filling in usernames and passwords, and it doesn’t take many seconds for scammers to log in and alter passwords.
It’s in opposition to this type of menace that two-factor authentication and two-step verification shield you. Two-factor authentication signifies that to log in, you want two several types of proof. One is normally one thing you realize (a password), the opposite can both be one thing you might have — comparable to a {hardware} key or your cell phone — or one thing distinctive to your bodily particular person, i.e. biometric authentication comparable to fingerprints.
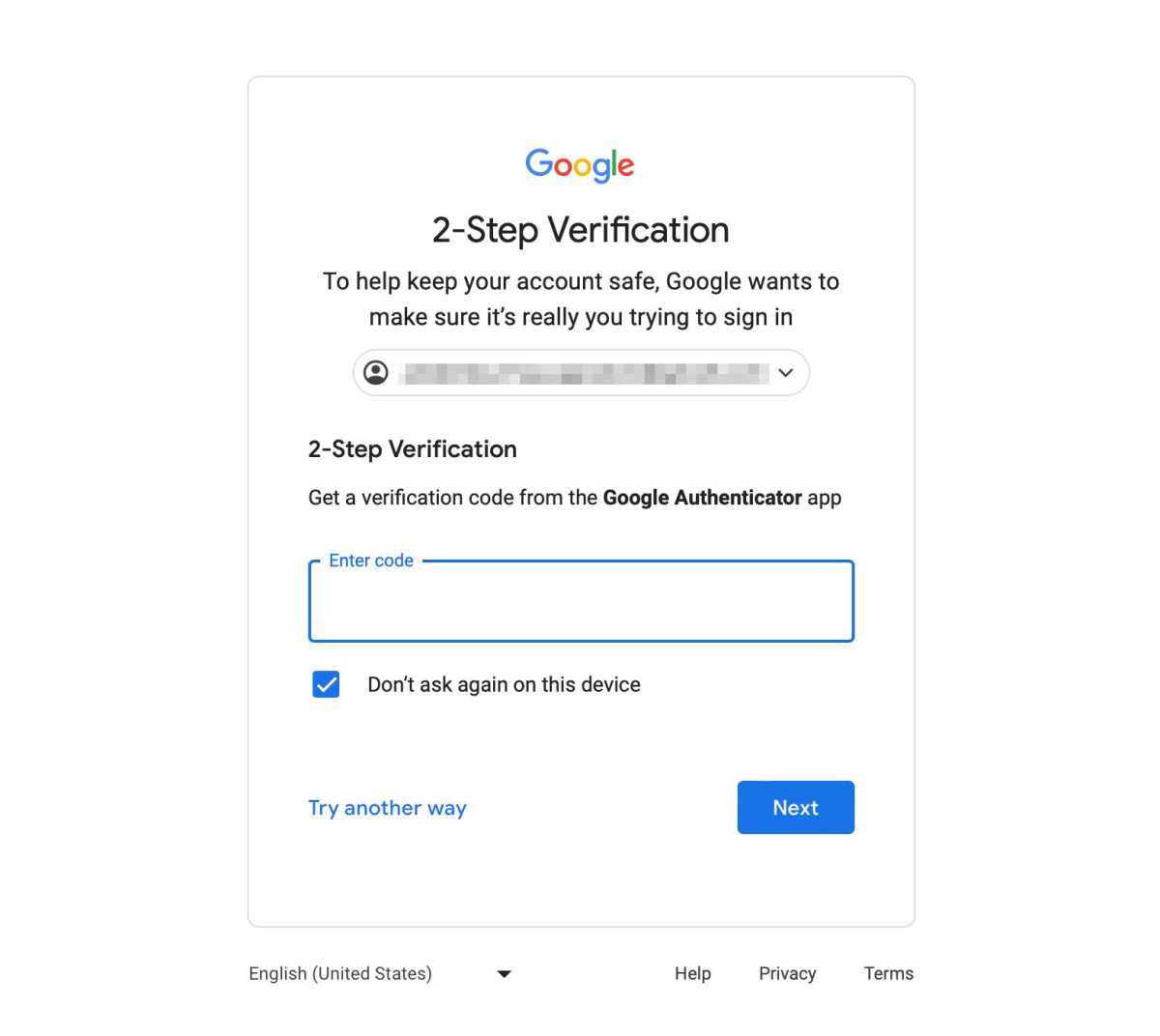
Two-step verification signifies that after filling in a password, you additionally need to fill in a code that’s despatched to your cell phone quantity, for instance by textual content message or electronic mail.
A standard resolution is using so-called “totp codes,” time-bound codes that can be utilized with particular apps (comparable to Google Authenticator) or in password managers. Since you should have bodily entry to the pc or cell phone the place the code generator is saved, it is a type of two-factor authentication. In addition, the gadget normally has a password or biometric unlock, and password managers all the time have a grasp password.
My advice for many customers who should not significantly weak by work or non-profit actions is to make use of the password supervisor to each retailer the login particulars and generate totp codes. It’s not as safe in absolute phrases as having a separate app for the totp codes, however so long as you’ve chosen one of many higher password managers, the dangers are very small.
What you get in change for the marginally greater threat is a a lot easier workflow when logging into totally different accounts, because the password supervisor normally robotically copies the totp code to the clipboard when it fills within the password and all you need to do is paste the code within the subsequent step. This, in flip, signifies that it doesn’t harm to allow two-factor authentication on as many accounts as potential, as an alternative of solely doing it on crucial ones, with the outcome that your total safety is way greater.

Foundry
Keep monitor of hacked websites and leaked credentials
Whether you solely began utilizing the web extensively within the 2010s otherwise you’ve been hanging out on-line because the early days, you’ll in all probability have the occasional account that’s a couple of years outdated.
These accounts, particularly in the event that they’re accounts you don’t log into fairly often, could have been leaked when the supplier was hacked sooner or later, with out your information. Most firms power all customers to alter their passwords after a breach, no matter whether or not the hackers really obtained the passwords, however if you happen to don’t log in, it’s possible you’ll not get a warning about it.
As effectively as the danger that somebody could have gotten into that specific account, for instance if you happen to used a weak password (which was straightforward to do way back earlier than password managers have been commonplace), leaks like this imply that the e-mail handle you used finally ends up on lists that varied criminals can use to ship out mass phishing or different assaults.
On the Have I Been Pwned web site, you may enter your electronic mail handle and rapidly discover out if it’s included in any of the databases of account particulars which were leaked following varied hacks. The web site lists all of the leaks your handle is included in, and the date of the hack. You can then test these websites to see if you happen to can nonetheless log in and if you could change your password.
Some password managers have options to robotically preserve monitor of hacked websites, for instance by partnerships with Have I Been Pwned. The program can see if you created the account and if you final modified your password, and shows a warning if you happen to haven’t modified your password since earlier than the location in query was hacked.
Security questions, the proper method
In the previous, earlier than two-factor authentication turned commonplace, many websites used safety questions that you simply needed to reply to get into your account if you happen to forgot your password, for instance, or to alter your password or electronic mail handle. This is much less widespread as we speak, however nonetheless occurs. The questions are sometimes alongside the traces of “what city were you born in”? and “what was the name of your first pet?”.
The trick with such questions is to not reply actually. Totally fictitious info can’t be guessed at and no hacker can discover out by, for instance, snooping round on Facebook or in some outdated weblog you wrote a very long time in the past. If you might have a password supervisor — which I extremely suggest — you may create a safe word the place you write down all of the questions and solutions.
If it’s an organization that you simply may keep up a correspondence with by telephone, it is sensible to decide on solutions which might be straightforward to pronounce and/or spell and within the language of the corporate’s customer support workforce.
Foundry
Log in with Google/Apple/Facebook
Nowadays, it has grow to be widespread for websites to not require you to create a brand new account with an electronic mail handle and password, however to give you to log in through an account with another person. The most typical are Google and Facebook, however Microsoft, Apple, Github and varied different websites additionally exist.
As lengthy because the account with the bigger firm is admittedly safe with a powerful, distinctive password and two-factor authentication, this may scale back the danger of the smaller firm’s account being hacked. If you don’t like password managers, this makes a whole lot of sense because it tremendously reduces the variety of passwords you could memorize or write down on paper.
The first time you log on this method, the web site creates an account for you, and you should comply with share sure info from the account with the opposite firm. For instance, Google shares your identify, your electronic mail handle, and your profile image (you probably have one).
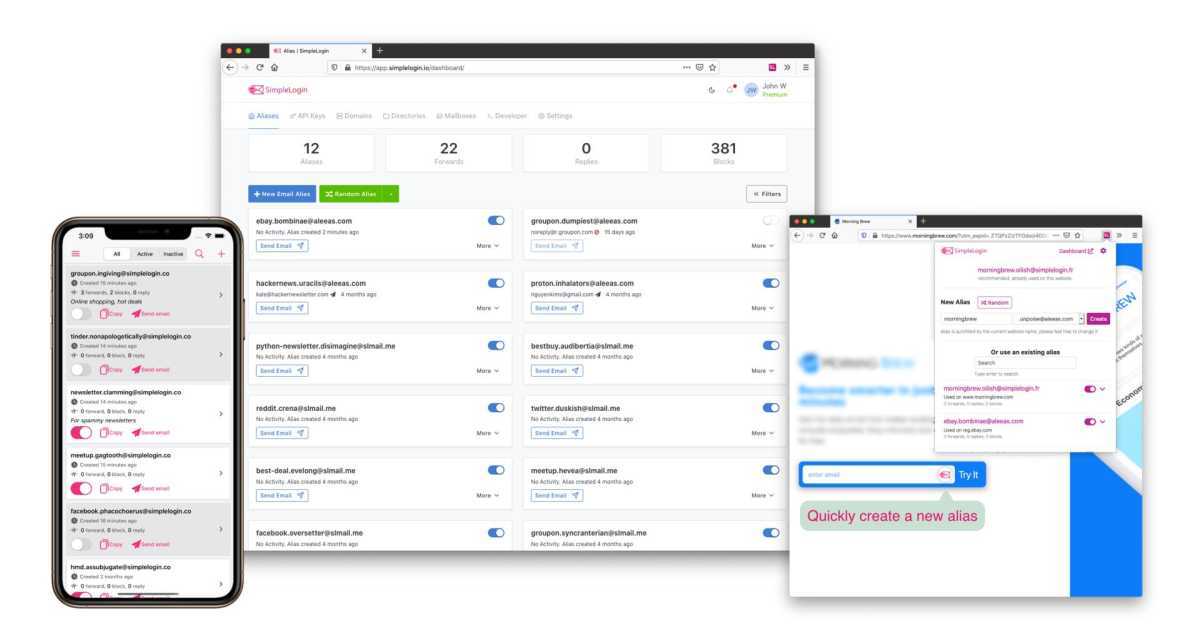
Simple Login
Unique electronic mail addresses for login
Because electronic mail addresses are so typically used as usernames and so typically leaked when firms are hacked, your electronic mail handle is a safety threat. Hackers can solely attempt to get into your accounts in the event that they know your username, and if you happen to’re like most individuals, you employ the identical electronic mail handle as your username on many or your entire accounts.
In latest years, providers have emerged that attempt to treatment this. Some electronic mail providers have a characteristic to create aliases, i.e. different addresses that additionally result in you, however this rapidly turns into cumbersome and most solely have a restricted quantity. Apple has limitless numbers for iCloud Plus subscribers. The password managers 1Password and Proton Pass have built-in options that robotically create aliases for brand new accounts. The SimpleLogin service additionally gives limitless aliases and the power to make use of your individual domains for $30 a yr.
Regain management of hijacked accounts
All the foremost tech giants have developed processes to assist customers regain entry to accounts. Search for the corporate or service identify and “account recovery.” Do this on a tool that you’re completely positive isn’t hacked or affected by malware, comparable to a pal’s laptop or an outdated laptop you might have wiped and reinstalled the system on.
The stage of issue varies and relies upon partly on how a lot hassle the hacker has brought about. For instance, a very thorough hacker can change each your electronic mail handle and telephone quantity. In some instances, and with some firms, you may hit the wall and need to accept shedding your account. Others have protections in opposition to that too. Facebook, for instance, sends a particular restoration hyperlink to the outdated electronic mail handle if somebody modifications their handle.
Once in, change your password and be sure to have the right electronic mail handle and telephone quantity. Reset any two-factor authentication and set it up once more, or set it up if you happen to didn’t have it earlier than. Some providers have a characteristic to log off of all of the gadgets you’re logged in to — use it!
Keys are the long run
A brand new expertise that has began to roll out due to the complete assist of each Apple and Google is passkeys. It includes utilizing uneven encryption in a intelligent method that makes it inconceivable for hackers to get into your accounts with out entry to your gadgets and passwords or biometrics to unlock them. Keys additionally shield in opposition to post-hack leaks, as the info saved on the server is meaningless with out entry to your gadgets.
This article was translated from Swedish to English and initially appeared on pcforalla.se.
[adinserter block=”4″]
[ad_2]
Source link