
[ad_1]
With these free on-line instruments, you’ll be able to instantly verify whether or not your electronic mail tackle has been leaked on the web and is related to stolen information. One of the 2 instruments, haveibeenpwned, has simply acquired a huge update with over 70 million new compromised electronic mail addresses.
haveibeenpwned by Troy Hunt
On haveibeenpwned you’ll be able to have your electronic mail tackle checked by the operator Troy Hunt to see whether or not it seems on the web in reference to leaked information. The web page reveals you the results of the verify instantly. See the next screenshot:
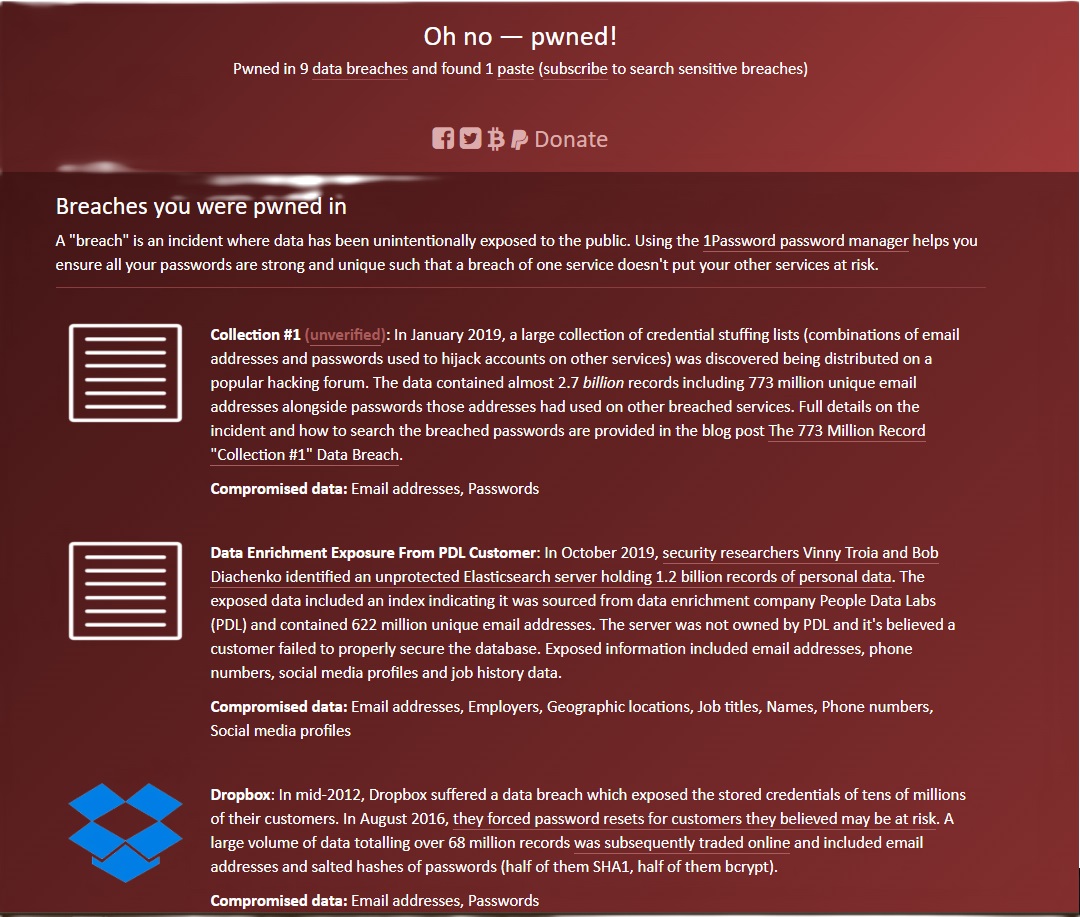
Foundry
The outcome offers recommendations on the best way to enhance the safety of the affected mail account and explains wherein breaches your mail password was found. The website additionally presents the choice of checking phone numbers to see whether or not they seem in breaches. You may also seek for stolen passwords. You may also be notified mechanically in case your electronic mail tackle saved with haveibeenpwned seems in a breach.
Important: Even in case your electronic mail tackle doesn’t seem in a knowledge leak, this doesn’t imply that it has not already been hacked or is just not straightforward to hack — for instance, due to a weak password. On the opposite hand, it doesn’t essentially imply that your electronic mail tackle is already being misused whether it is included in a breach.
Operator Troy Hunt is a security consultant from Australia. He additionally runs a Twitter channel on information leaks on the internet.
Tip: How to keep away from electronic mail stalking and defend your privateness
It is theoretically true that haveibeenpwned could be misused below sure circumstances, by permitting anybody to enter your electronic mail tackle and doubtlessly uncover which cloud providers you may have registered with utilizing that tackle (e.g., Dropbox within the picture above). However, customers who log in to doubtlessly suspicious on-line providers equivalent to porn portals or on-line intercourse contact platforms with their skilled or major and usually identified electronic mail tackle are appearing extraordinarily carelessly. For such functions, it’s best to create a further, well-disguised electronic mail tackle whose title can’t be used to infer your personal id.
By the way in which: Firefox Monitor additionally makes use of haveibeenpwned.
HPI Identity Leak Checker
The HPI Identity Leak Checkerk from the Hasso Plattner Institute for Digital Engineering is one other free on-line software that you should use to verify your electronic mail tackle to see whether or not it seems in breaches. Here, nonetheless, the results of the verify is just not displayed straight on the HPI Identity Leak Checker web site, however as a substitute the HPI Identity Leak Checker sends an electronic mail with the verify outcome to the checked electronic mail tackle, see screenshot:
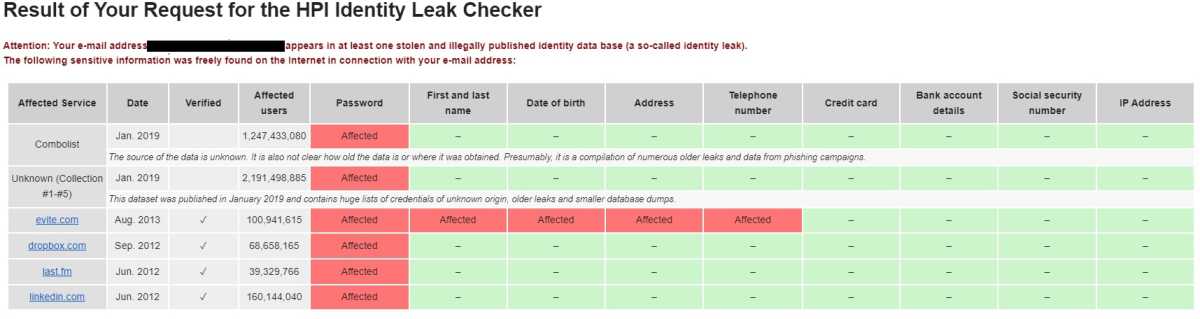
Foundry
This signifies that HPI Identity Leak Checker can’t be used for stalking as with haveibeenpwned.
It is operated by the Hasso Plattner Institute (HPI) on the University of Potsdam. You can discover particulars on the way it works within the FAQ. Important: “The Identity Leak Checker only provides information on whether your password was found in a leak. The Leak Checker says nothing about whether this password still works for the affected user account. As your password can still be found in the corresponding leak, the website will continue to issue a warning.”
Identity Leak Checker of the University of Bonn
The University of Bonn also offers a leak checker. It works in precisely the identical means because the HPI’s: You enter the e-mail tackle to be checked and the evaluation is then despatched to the e-mail tackle you entered. This additionally prevents stalking or spying makes an attempt, as is theoretically doable with haveibeenpwned.
The Bonn Leak Checker was developed as a part of the EIDI undertaking, which is backed by the German authorities.
How to react accurately
If the instruments talked about above present you that your electronic mail tackle seems in information leaks/breaches, it’s best to change your password instantly. If you may have used the identical password that you simply use on your electronic mail account for different providers, you must also change this password there.
Very necessary: Install two-factor authentication if that is supported on your electronic mail account.
It’s additionally extremely beneficial that you simply use a password supervisor to create and save distinctive, safe passwords for all of the websites and providers you employ. See our information to the best password managers for ideas.
Where do the stolen electronic mail addresses come from?
Most stolen electronic mail addresses originate from assaults on firm servers that run providers with which you may have registered your electronic mail tackle. For instance, cyber criminals stole the info of a number of hundred thousand clients of the Hessian vitality provider Entega. These information treasures are then provided on the market by the thieves in web boards or on the darknet. Other main information thefts at firm stage embrace, for instance:
You are powerless towards such information leaks, that are attributable to stealing server information; you can not stop them. But you’ll be able to take measures to reduce the harms.
This article was translated from German to English and initially appeared on pcwelt.de.
[adinserter block=”4″]
[ad_2]
Source link