
[ad_1]
An assault in your Wi-Fi community will not be like a financial institution theft: Instead of masked robbers blowing open the vault with a loud noise, a hacker inconspicuously approaches the router, searches for weak factors and tries out a number of assault paths. Or he exploits a recognized safety gap by unleashing an assault on the router that has been ready for this goal.
Because you by no means know when and the place your router will grow to be a goal, you must all the time be sure that the machine is protected towards hacker assaults: Increase the safety stage of the router with appropriate settings in order that an assault is simply too expensive for the hacker. And hold your self repeatedly knowledgeable about safety gaps with the intention to plug them with firmware updates.
We present you ways probably the most harmful Wi-Fi community assaults work and how one can shield your self towards them: This means you instantly have the correct reply to hacker assaults at hand and might safe your router and residential community in just some easy steps.
Further studying: How to secure your home Wi-Fi network and router
Why hackers assault your Wi-Fi community
To assault a Wi-Fi community, hackers both assault the Wi-Fi connection between shopper and router or they assault the router straight.
With the primary technique, the attackers wish to document information that the units change through Wi-Fi: In this fashion, they will first guess the Wi-Fi key with the intention to then connect with the connection or redirect it. In this fashion, they acquire entry to delicate info reminiscent of passwords for on-line banking or on-line accounts. They can then use these themselves or promote them to different hackers.
In addition, attackers can log on through your web entry to obtain copyrighted materials, for instance, or to hold out different felony acts that can’t be traced again to the hacker, however solely to you.
If attackers take over the router, all units within the community are open to them: They can, for instance, manipulate good residence units that management lights, heating, or the alarm system. In addition, they will attain information on computer systems or NAS units on this method, which they encrypt through ransomware with the intention to extort a ransom.
In most circumstances, a hijacked router turns into a part of a botnet that hackers use to assault different targets, reminiscent of inside networks of presidency companies or corporations. But even when an assault has much less formidable targets, it may be annoying: For instance, a neighbor who has the enjoyable of disrupting your community and on-line connections with a Wi-Fi assault. Or members of the family who hope to override parental management settings or web site filters by gaining unauthorized entry to the router.
Deauthentification: The first assault on the Wi-Fi community
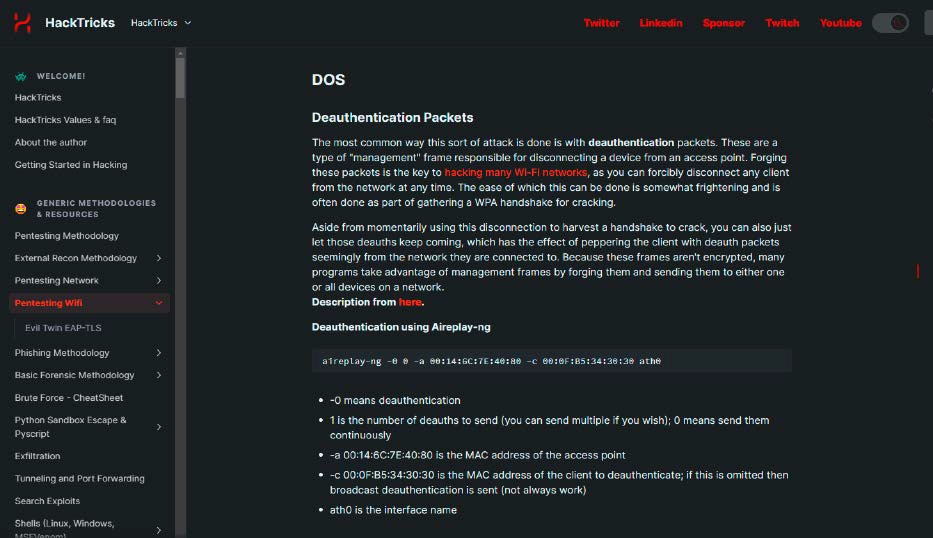
Deauthentification is among the customary assaults towards the Wi-Fi
community: How and with which instruments hackers proceed is described intimately on quite a few web sites.
IDG
This is how the assault works: With a deauthentication, the hacker interrupts the connection between the router and a shopper. This logoff course of is a standard and standardized process in WLAN: A router, for instance, sends a deauthentication message to a shopper that has not been energetic within the Wi-Fi community for a while, in order that it doesn’t have to take care of this connection unnecessarily.
With band steering or AP steering, the router can even forcibly deauthenticate a shopper in order that it subsequently connects through a sooner Wi-Fi frequency or with a repeater that gives it with a greater Wi-Fi sign.
In the case of the deauthentication assault, the request to log out doesn’t come from the router, however from the hacker. To do that, he manipulates a corresponding information packet: It incorporates the MAC tackle of the router and a shopper. In addition, the attacker should know the SSID of the attacked Wi-Fi community. If he additionally finds out the radio channel, the assault is much more focused.
This is what the hacker needs to attain: Deauthentication is the premise for many Wi-Fi community assaults. The attacker can, for instance, interpose himself when the shopper needs to reconnect to the router after the pressured logoff. The two units change messages with which they affirm to one another that they know the agreed WLAN password with out transmitting it straight. Then they outline the keys with which the next information switch is secured (4-way handshake).
With an appropriate instrument, the attacker intercepts the info site visitors through the login, with which he tries to guess the Wi-Fi password. You can learn extra about how that is executed within the part “Brute force attack” beneath. The Evil Twin assault additionally begins with a deauthentication assault.
However, the hacker can even completely interrupt the connection between a shopper and the router (DoS, Denial-of-Service): To do that, he constantly sends deauthentication packets to the shopper, which due to this fact can’t attain the router. In a non-public community, good residence units reminiscent of alarm programs or surveillance cameras could be paralyzed on this method.
How to fend off the assault: The deauthentication packets should not encrypted, so the attacker doesn’t want a Wi-Fi or community password to ship them, however solely the Mac addresses and the WLAN SSID, that are simple to search out out on a community.
You can forestall this by activating the Protected Management Frames (PMF) operate: The easiest method to do that is with WPA3. PMF is a compulsory half of the present safety customary. If you turn it on within the router, it additionally transmits the deauthentication packets with a standard key in order that the shopper is aware of that they really come from the router it is aware of.
However, if the shopper doesn’t assist WPA3, this measure won’t provide help to. However, PMF can be used along with WPA2 on many routers: With the Fritzbox, for instance, you’ll be able to moreover activate PMF if you choose the choice “Activate support for protected logins of WLAN devices (PMF)” within the menu underneath “WLAN > Security.”
Brute pressure assault: How hackers crack your Wi-Fi password
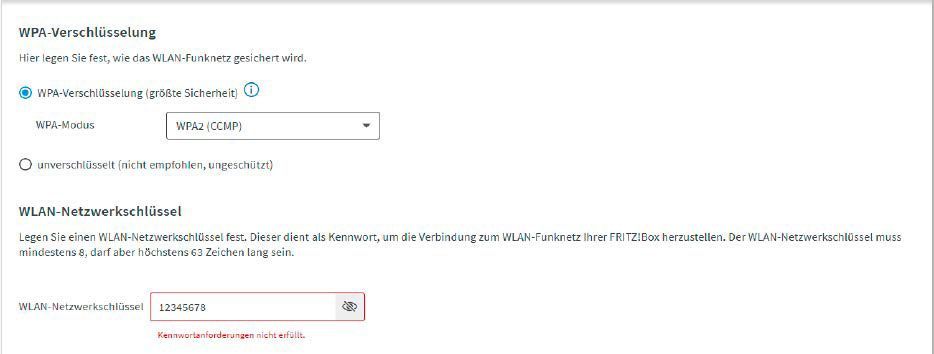
A robust Wi-Fi password makes brute-force assaults tougher as a result of the hacker wants too lengthy or too many computing assets to determine it out. Many routers will warn you to a password that’s too weak.
IDG
This is how the assault works: All encryption within the Wi-Fi community derives the units concerned in a connection from the WLAN password they know. If, for instance, after a deauthentication assault, the attacker cuts the info switch to re-establish the connection, he can use it to infer the password.
Usually, this doesn’t occur straight after the interception, however the attacker unleashes a strong pc with a robust CPU and GPU on the recording, which tries out completely different passwords in fast succession that might match it. He can pace up this course of through a web based service that makes use of a number of servers for this goal. Dictionaries, databases with well-liked passwords, and character mixtures function the premise for this assault.
In a masked assault, the attacker units sure defaults that he believes match the Wi-Fi key — for instance, that the primary letter within the password is written in capital letters or that half of the password consists of numbers. This significantly reduces the hassle required to crack the password: For instance, guessing a nine-digit password within the type Anton1970 would take a number of years if the attacker needed to check out all attainable mixtures of letters and numbers. If he speculates that the password consists of a reputation and a 12 months, he’ll reach lower than an hour.
This is what the hacker needs to attain: If the attacker is aware of the Wi-Fi password, all doorways within the residence community are open to him. For instance, he can infiltrate his personal purchasers to achieve entry to different residence community units and shares. In addition, the whole information site visitors can then be recorded with out encryption.
How to fend off the assault: The above instance clearly reveals that the longer and extra difficult a password is, the tougher it’s to crack. Therefore, you must positively keep away from predictable phrases or numbers reminiscent of identify, tackle, 12 months of delivery, and so forth. in your Wi-Fi password. Special characters additionally improve the complexity of the password. In this case, a shorter password with eight to 12 characters is ample, however its elements of higher and decrease case letters, numbers, and particular characters are chosen utterly randomly — for instance z9!qO6+B§.
Also necessary: Do not use the password for one more login, for instance to a web based account: If the supplier of the account is hacked, the stolen passwords normally flip up shortly on the web, and a community attacker can then use them for a brute pressure assault.
Further studying: Best password managers in 2023
Evil Twin: If the hacker locations a false entry level
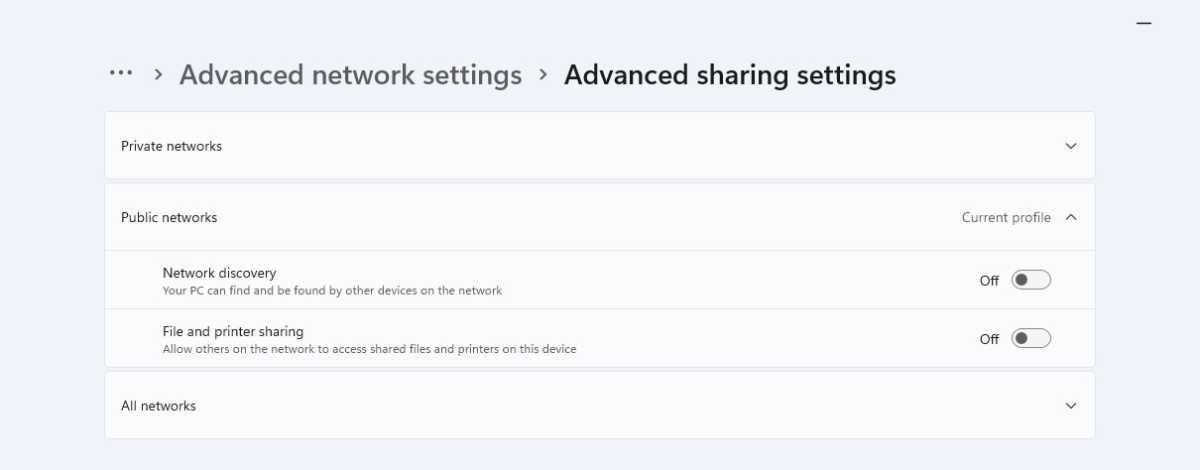
Deactivate the automated Wi-Fi login on a Windows pocket book if you find yourself in a public sizzling spot. This will increase safety towards an Evil Twin assault.
Foundry
This is how the assault works: You are notably in danger for this assault in a public Wi-Fi community. But this assault can be attainable at residence. The hacker units up a router or entry level that makes use of the identical SSID because the common router. This can simply be discovered through a community scan. An attacker can proceed in an analogous method with a honeypot assault: To do that, he gives WLAN in a spot that has no web entry, however the place this isn’t instantly noticeable: For instance, if he units up a faux entry level with the SSID “Pizzeria” in an Italian restaurant.
Both assaults can simply be carried out with a pocket book or smartphone, so long as the shopper that connects can even entry the web through it. The attacker will increase his possibilities of success if he locations the false entry level in such a method that it gives a greater sign power than the true one. He can even use a deauthentication assault to get purchasers to log out from the true entry level after which connect with the faux one. With an unsecured Wi-Fi community, the hacker doesn’t should do the rest. If there’s a Wi-Fi password, the attacker may current the shopper with a manipulated login internet web page when making an attempt to attach with the intention to retrieve the password.
This is what the hacker needs to attain: With the Evil Twin, the hacker can monitor the shopper’s total information site visitors — for instance, the entry of passwords for on-line banking or buying. Since this assault is normally not seen instantly, the hacker has sufficient time to document sufficient information.
In addition, he beneficial properties entry to the shopper to seek for delicate information or to put in malware that provides him extra prospects to manage the machine.
This is how one can shield your self: In precept, you shouldn’t do something on a public Wi-Fi community that requires you to enter an necessary password. If that is obligatory, you have to make completely certain that you simply set up an encrypted connection to the corresponding web site: You can recognise this by the truth that the online tackle begins with https://.
The finest safety towards assaults in a public Wi-Fi community is a VPN that connects you to your router at residence: This encrypts all information that you simply ship through the general public WLAN.
Further studying: The best VPN services in 2023
You must also keep away from utilizing Wi-Fi networks that don’t require a password. It can be finest to modify off the shopper in order that it mechanically connects to recognized WLANs: Otherwise, it is going to mechanically contact each entry level inside vary that makes use of a recognized SSID — even when it’s a false one. Deactivate the automated WLAN registration on a Windows pocket book in case you are in a public hotspot. This will increase safety towards an Evil Twin assault.
Router assault: How hackers exploit safety gaps
This is how the assault works: The router is crucial machine in your Wi-Fi community and due to this fact a gorgeous goal for hackers. Many fashions facilitate these assaults by safety gaps within the firmware: In most circumstances, it’s based mostly on Linux, which is why router producers don’t program all of the capabilities themselves, but additionally depend on quite a few open-source applications which will include bugs.
In addition, some producers fail to exchange or take away from the firmware outdated firmware modules which might be not maintained by programmers. These gaps enable attackers, for instance, to have program instructions executed on the router, because it doesn’t examine or filter these manipulated inputs. This can instruct the router to execute ready scripts that give the attacker complete management. Depending on the firmware hole, an attacker have to be linked to the router through Wi-Fi or distant entry to do that.
This is what the hacker needs to attain: By technique of a safety gap, the attacker can utterly take over the router with the intention to change settings or change off safety capabilities. In many circumstances, this serves to make sure everlasting however unnoticed entry to the router menu. The attacker could make the hijacked router a part of a botnet with which he assaults different networks, for instance, through a DoS assault or to ship spam messages.
How to guard your self: Regularly examine whether or not new firmware is obtainable in your router. It can be a good suggestion to repeatedly examine necessary safety web sites that report on router vulnerabilities and to go to the assist pages in your router mannequin.
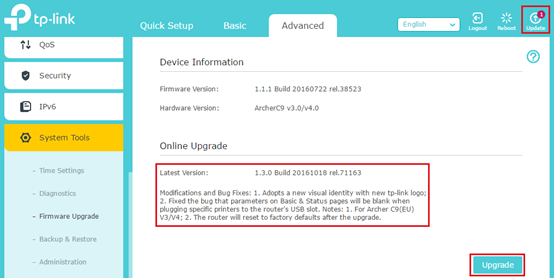
It’s necessary to maintain your router firmware updated. Some routers even supply a setting to mechanically updgrade firmware.
TP-Link
Remote assault: Access to the router through the web
This is how the assault works: Many customers have set their router in order that its settings can be accessed from the web. Therefore, hackers can even discover these routers with a community scan, as a result of distant entry normally takes place through customary ports, reminiscent of port 443. Similar to cracking the Wi-Fi password, the attacker then tries to search out out the entry info — for instance, through a brute pressure assault.
This is what the hacker needs to attain: In the menu, the hacker adjustments settings that give him management over the router. In this fashion, he can combine it right into a botnet or redirect the web entry of Wi-Fi purchasers to a manipulated server, for instance, by storing corresponding DNS settings: In this fashion, passwords could be tapped or malware could be infiltrated into the house community.
How to guard your self: It is finest to activate distant entry to the router solely whenever you completely want it. It is totally necessary to have a robust password for logging into the router menu.
The router must also have the ability to supply to arrange a person account for distant entry that’s completely different from the one for native entry.
For extra safety, an IP tackle vary can usually be outlined: Only units with an identical IP tackle can then entry the router menu remotely in any respect. Many routers additionally lock the menu after a sure variety of failed logins or lengthen the time interval after every failed try till somebody is allowed to log in once more.
This article was translated from German to English and initially appeared on pcwelt.de.
[adinserter block=”4″]
[ad_2]
Source link