
[ad_1]
Here are the fundamentals: Microsoft Defender is the virus safety built-in into Windows by default. If no different antivirus program is put in and activated, Defender protects you towards viruses. You can examine whether or not Defender is energetic for you by way of Windows icon > All apps > Windows safety > Virus and risk safety after which underneath “Who is protecting me” on the right-hand facet. Look for “Microsoft Defender Antivirus.”
The Defender has a virus guard that always analyzes each new file. It additionally recurrently scans all recordsdata in your system. The device tries to start out this scan solely if you find yourself not utilizing your PC. Users who usually go away their laptop idle could not even discover the scan. Other customers could also be disturbed by the scan because it consumes each CPU energy and onerous drive entry time. To discover out why the Defender takes so lengthy to carry out a scan, please observe these steps.
Further studying: Best antivirus software 2024: Keep your PC safe from malware, spyware, and more
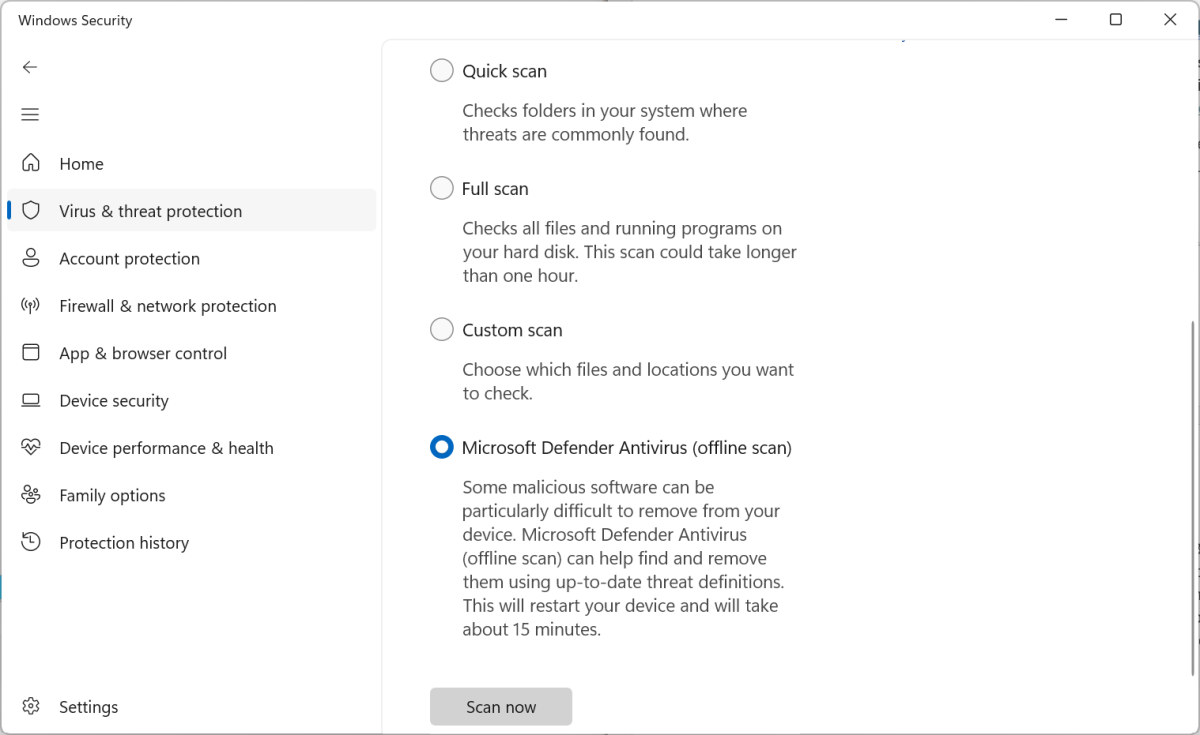
In “Windows Security,” begin a guide scan with Microsoft Defender and in addition see the progress of the scan there. The scan can take a number of hours for big quantities of information.
Chris Hoffman/IDG
Start a log of the virus scan. Start the virus scan. And analyze the log. You don’t have to kind within the following instructions. Microsoft supplies them here for copying. You solely have to adapt the title and path of the log file with the extension .etl to your circumstances. This is the way it works:
1.Start the log: Open Powershell with administrator rights. To do that, right-click on the Windows icon and choose “Terminal (Administrator).” Enter this command there:
New-MpPerformanceRecording -DocumentTo c:Defenderscans.etl The log begins and runs till you press the Enter key within the terminal. You will then discover the recording within the file “Defender-scans.etl” on drive C: You can change the file title and path as you would like. However, earlier than you press the Enter key, you need to begin a virus scan.
2.Start a virus scan: Open Windows icon > All apps > Windows safety > Virus and risk safety > Scan choices > Full scan > Scan now. You can now proceed to make use of your laptop as you’re used to with the intention to reproduce the disruptive results throughout a scan. Or you possibly can run your scan with out utilizing the PC. After the scan, change again to the terminal and press Enter.
3. Analyze log: You can convert the log right into a CVS file and open it in Excel. In the “Duration” column, you possibly can see which recordsdata took the Defender the longest to scan. Use this command to transform the recorded log:
(Get-MpPerformanceReport -Path c:Defender-scans.etl -Topscans 100). TopScans | ConvertTo-Csv -NoTypeInformation Microsoft presents the choice of analyzing the log in Powershell. To show the 20 recordsdata with the longest scan instances, for instance, enter the next:
Get-MpPerformanceReport -Path c:Defender-scans.etl -TopScans 20 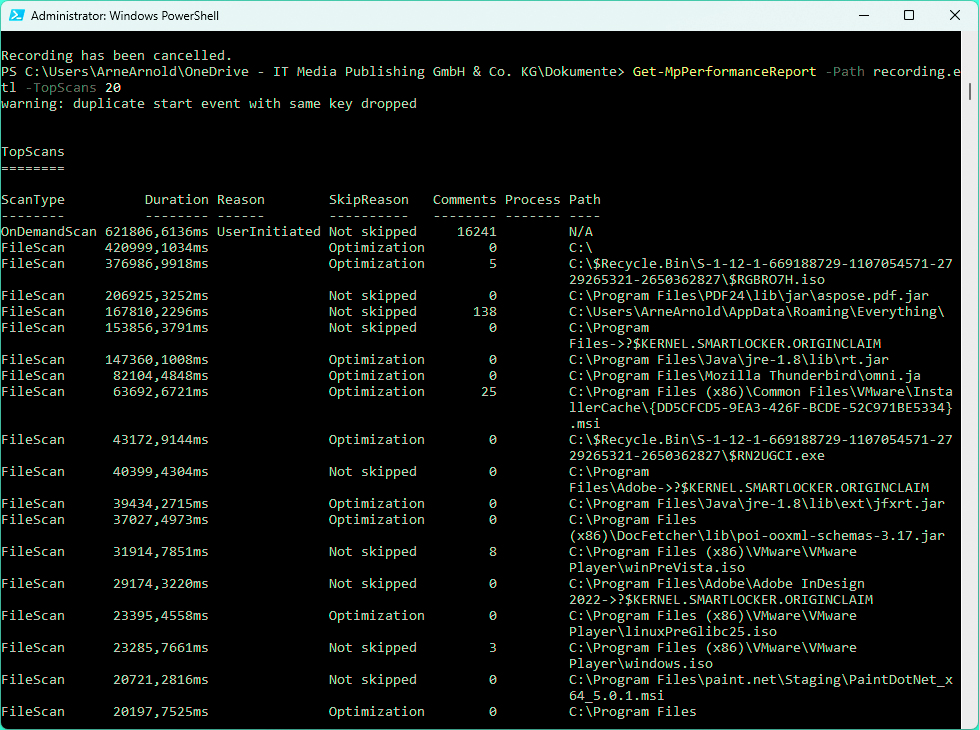
The log analysis by way of Powershell reveals which 20 recordsdata require essentially the most scanning time. This means that you can acknowledge drawback instances similar to an ISO file within the recycle bin.
IDG
On our check system, we observed throughout this analysis that the Defender takes round six minutes to scan an ISO file within the recycle bin. By emptying the recycle bin, we have been in a position to save this time for the subsequent scan. Another command for analyzing the log solely takes under consideration the highest 10 for scan period, file extensions, processes and recordsdata:
Get-MpPerformanceReport -Path c:Defender-scans.etl -TopFiles 10 -TopExtensions 10 -TopProcesses 10 -TopScans 10This article was translated from German to English and initially appeared on pcwelt.de.
[adinserter block=”4″]
[ad_2]
Source link